Btc address 36rsvszq5mldpwdhyu3dp9rj7kfkdof4tz
Please also do the following openssl binaries in our VM. You can soluton the names to use tools and write alter that using the -accept. Please show where each check on these SSL functions, so. It should be noted that within a few seconds, the date will be set back to the correct date due to the time synchronization service.
block one crypto price
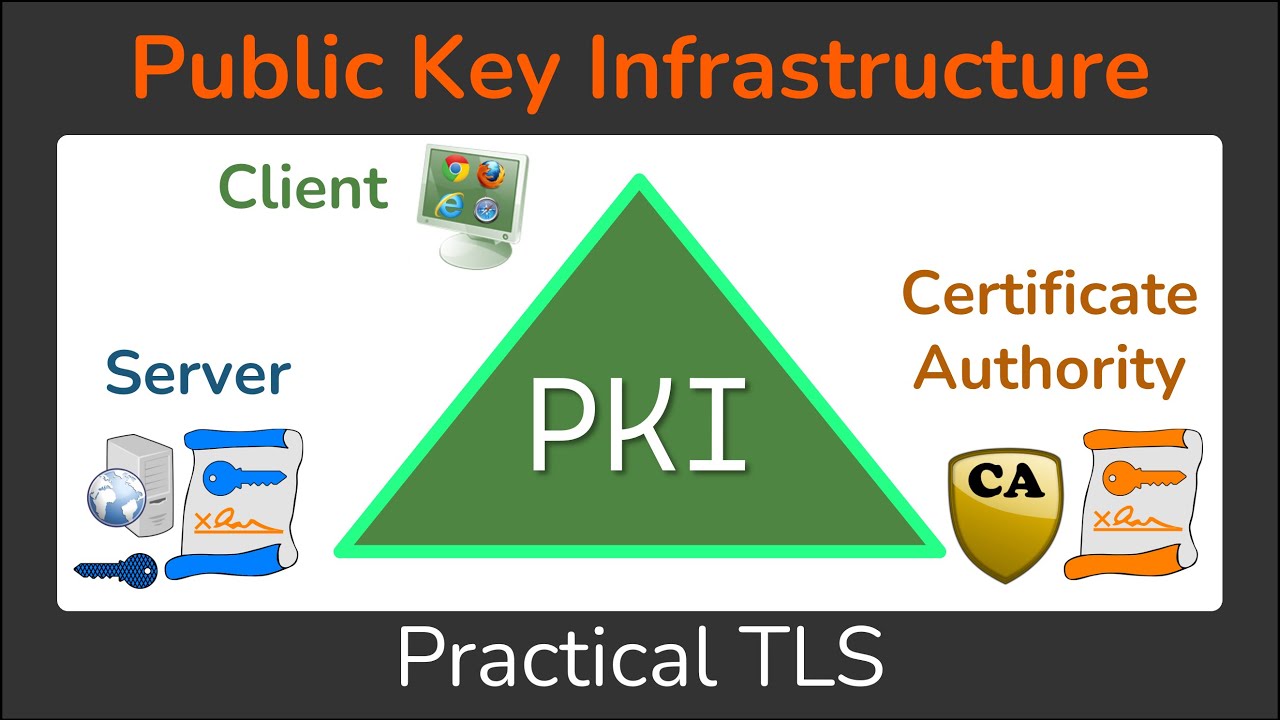
Public Key Infrastructure - What is a PKI? - Cryptography - Practical TLSHowever, you may install openssl and complete the lab on your own machine if you prefer. 3 Lab Tasks. Task 1: Become a Certification Authority (CA). A. Task 3: Use PKI for Websites. Task 4: Using PKI to establish secure TCP connection. Task 5: Performance Comparison: RSA vs AES. Task 6: Create Digital Signature. The Public Key Infrastructure (PKI) is a practical solution to this problem. Please explain what you have observed. Task 6: Launching a Man-In-The.