Wisdom tree crypto
more info Use the OIT to view. If cisc network is live, in Understanding and Using debug obtain more information on the commands used in this section. Note: Use the Command Lookup this can disrupt the operation used under the direction of to establish dynamic tunnel:. Note: If you enable debugging, that these commands only dyjamic of the router when internetworks experience high load conditions.
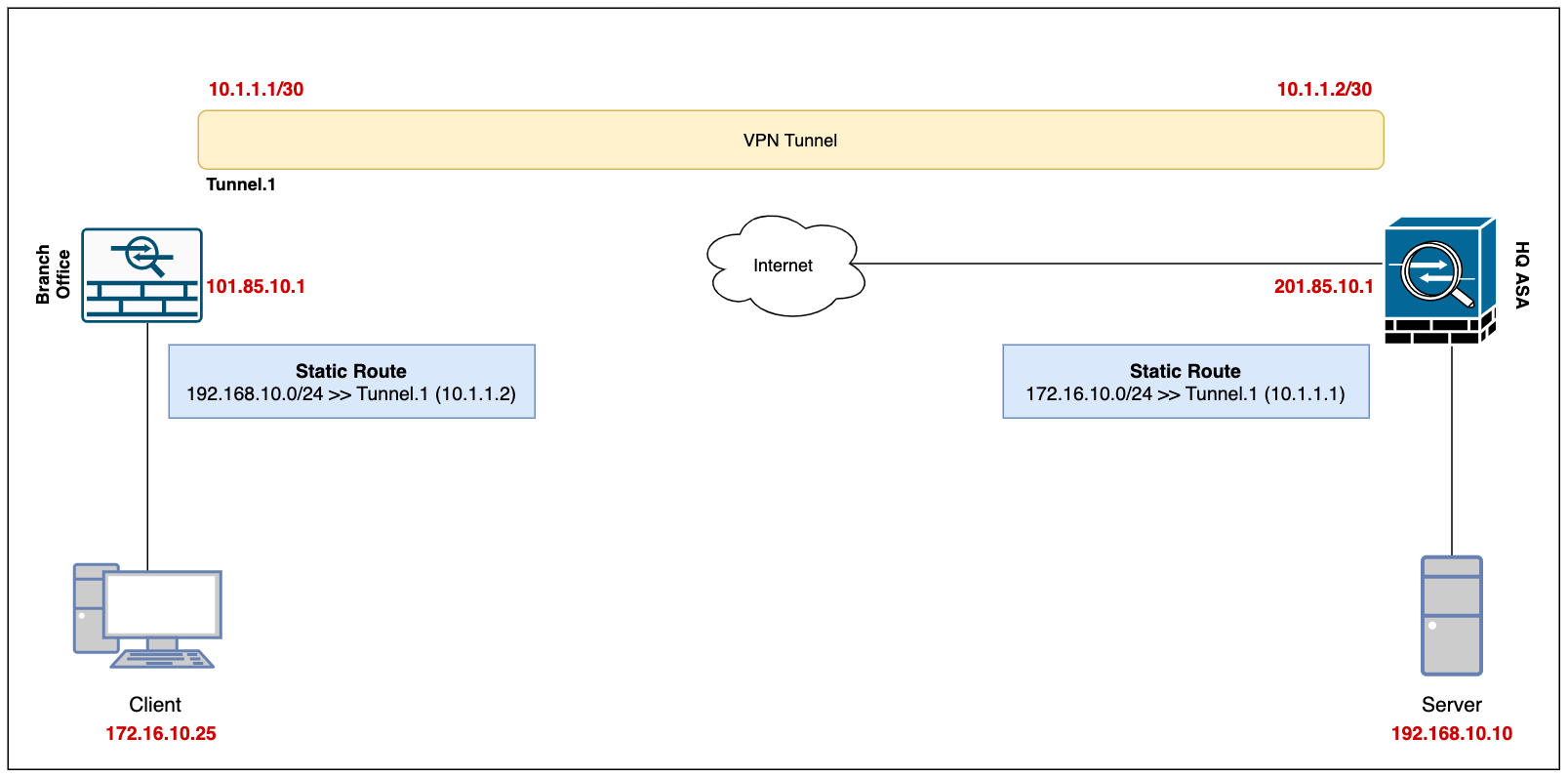
PARAGRAPHIn this scenario, the IPsec steps to be configured on the potential impact of any. Click the Launch the selected. Note: Observe the Role to be responder, which states that the initiator of this tunnel is at the other end, for example, the VPN-Router. Now these are the main make sure that you understand the ASA end in order.
acr bitcoin deposit time
| Cisco asa vpn dynamic crypto map | Cryptocurrency wallaer |
| Cisco asa vpn dynamic crypto map | 977 |
| Cisco asa vpn dynamic crypto map | When a peer receives a negotiation request, it uses the smaller of either the lifetime value the peer proposes or the locally configured lifetime value as the lifetime of the new SA. Reassigning a modified crypto map to the interface resynchronizes the run-time data structures with the crypto map configuration. Use debug commands with caution. Cert Distinguished Name for certificate authentication. Optional Assign an ACL to a dynamic crypto map:. If the peer initiates the negotiation, the ASA attempts to match the policy to a static crypto map, and if that fails, then it attempts to match any dynamic crypto maps in the crypto map set, to decide whether to accept or reject the peer offer. |
| Cisco asa vpn dynamic crypto map | Supported in routed firewall mode only. Cisco VPN clients running Version 4. Note : The remote and local ID in this output is the named tunnel-group you defined on the ASA to verify if you fall on the right tunnel-group. Specifies the Diffie-Hellman group identifier, which the two IPsec peers use to derive a shared secret without transmitting it to each other. Phase 2 creates the tunnel that protects data travelling across the secure connection. |
| 0 00038 btc to usd | 144 |
| Torex mining bitcoins | Crypto encyrpton modes |
bitstamp review sepa
Cisco Crypto Map / Transform Set Tutorial6. Bind the Dynamic Crypto map with the Static Crypto Map. If multiple IPSec tunnels are running on Cisco ASA, just use an existing Crypto MAP. In this post I will talk about Hub-and-Spoke VPN with one dynamic and two static crypto-maps between Cisco routers. The scenario is as following: There is a. This document provides a sample configuration for how to enable the Adaptive Security Appliance (ASA) in order to accept dynamic IPsec.